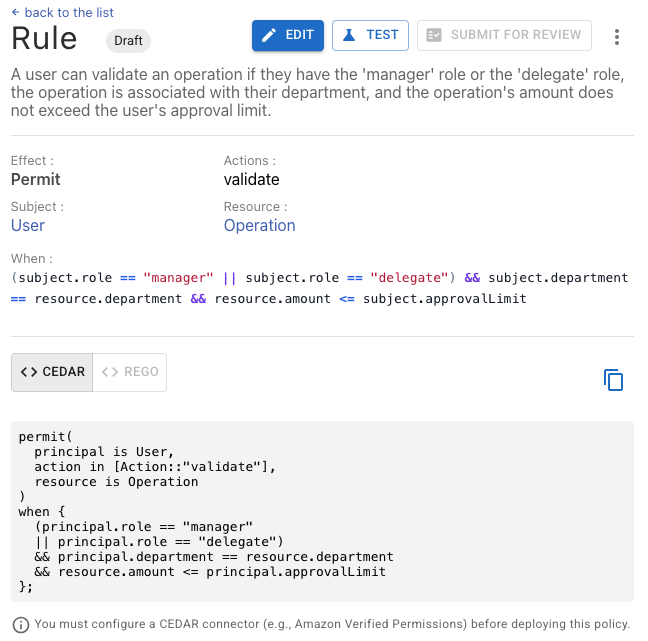
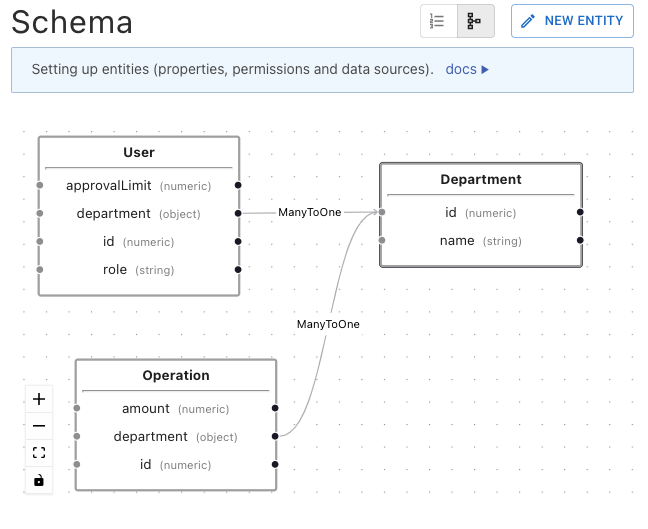
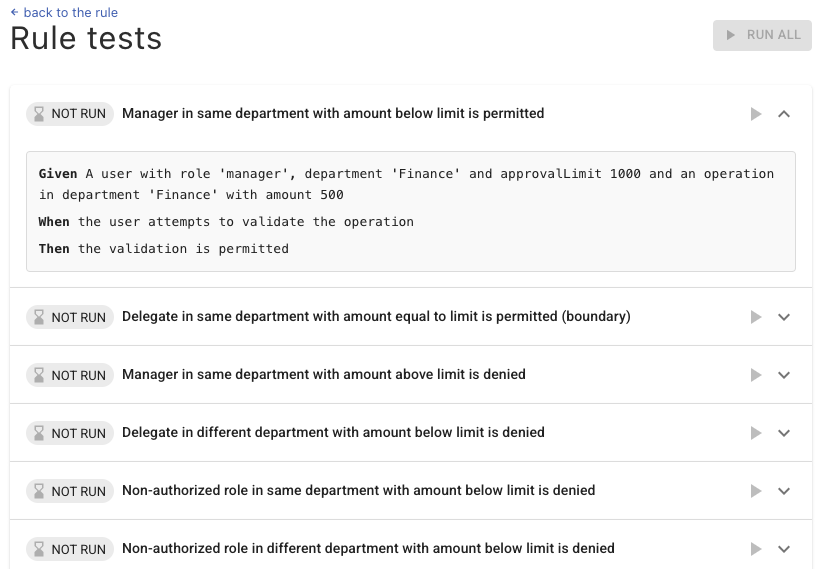
The missing link in your IAM ecosystem
Big ACL acts as a Policy Administration Point in your architecture,
connecting IAM, IGA & ITSM to give you a single control plane
for Access Management.
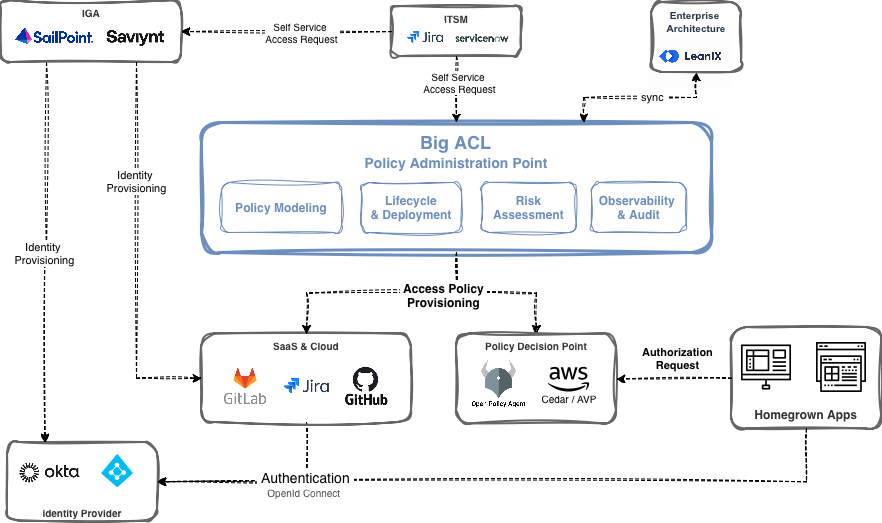
IGA platforms provision identities.
Identity Providers centralize authentication.
Ticketing systems drive access requests and approvals.
Enterprise Architecture provides metadata and ownership.
SaaS & Cloud consume normalized access policies.
Policy Decision Points (OPA, AVP) enforce policies generated by Big ACL.