Access Governance Platform
Regain control of your authorizations
One collaborative platform where security, product, and engineering teams define access policies and govern them end to end—in plain language everyone understands.
Access Governance Platform
One collaborative platform where security, product, and engineering teams define access policies and govern them end to end—in plain language everyone understands.

Author, control, publish — then improve
Big ACL structures your policy work into a clear, repeatable cycle. Security, product, and engineering teams collaborate at every stage — each iteration strengthens your access rules and reduces risk.
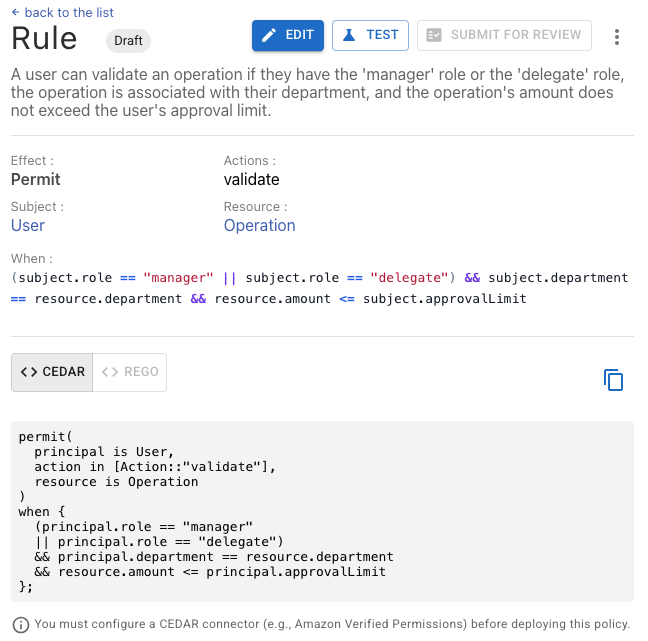
Define rules in plain language, model your entity schema, and structure your domain vocabulary.
Validate with auto-generated tests, detect conflicts, review with stakeholders.
Snapshot an immutable version, translate to Rego & Cedar, deploy to your environments.
Git for your access policies
Structured versioning for access policies. Every change is tracked, every version is a self-contained artifact that can be compared, audited, and rolled back.
Version diff view
3 rules added, 1 modified, 0 removed
Schema restructured, 12 rules migrated
Hotfix: approval limit threshold
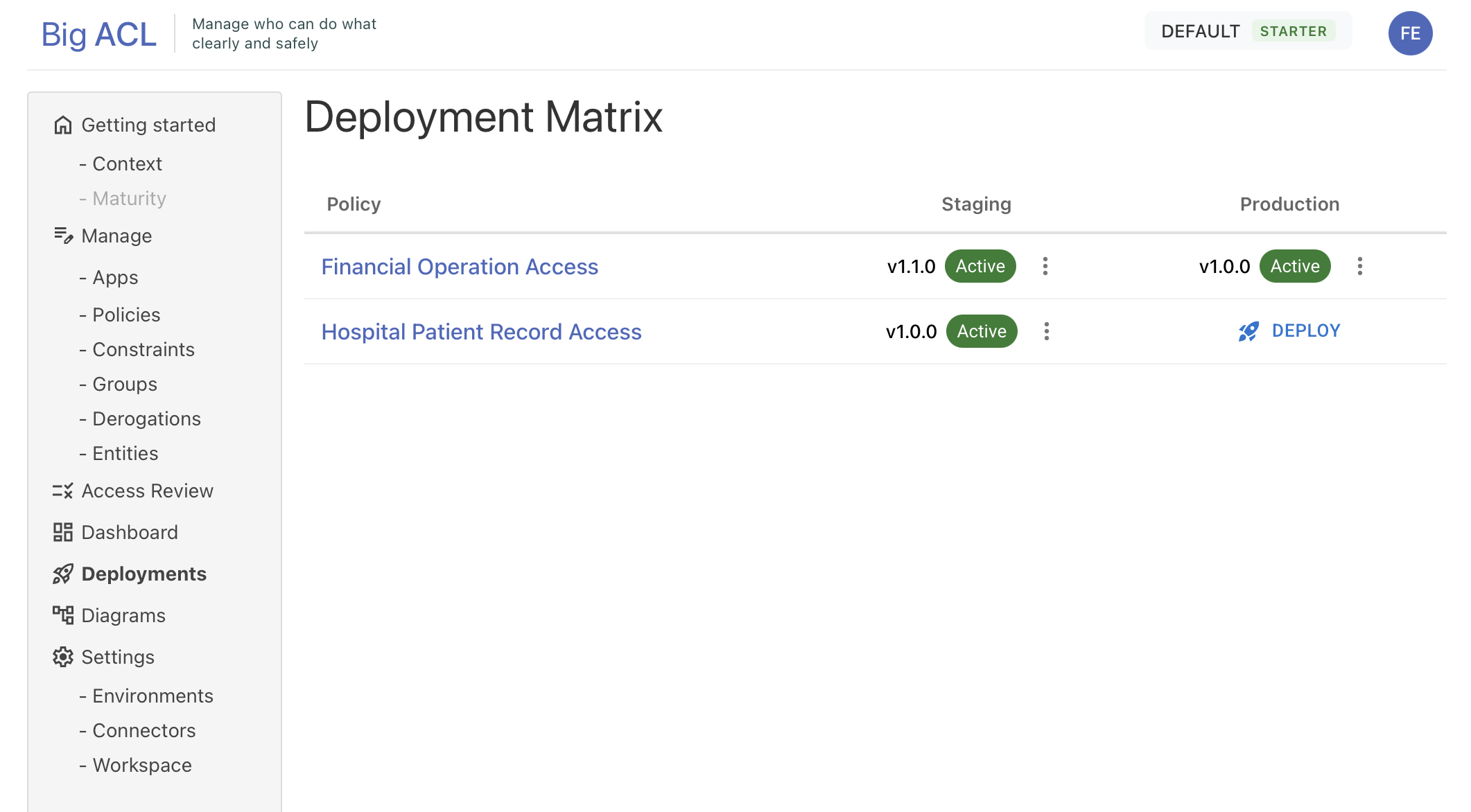
Promote with confidence, rollback in seconds
Big ACL gives you full control over the lifecycle of your policies — from impact analysis to multi-environment promotion and instant rollback.
See every decision, investigate any incident
Consolidated decision visibility across all your Policy Decision Points. One dashboard for every permit and deny, regardless of enforcement engine.
From policies to continuous access governance
Go beyond policy authoring. Big ACL connects your rules to the people who use them — with access reviews, expected rights analysis, and compliance reporting built in.
The missing link in your IAM ecosystem
Big ACL acts as a Policy Administration Point in your architecture,
connecting IAM, IGA & ITSM to give you a single control plane
for Access Management.
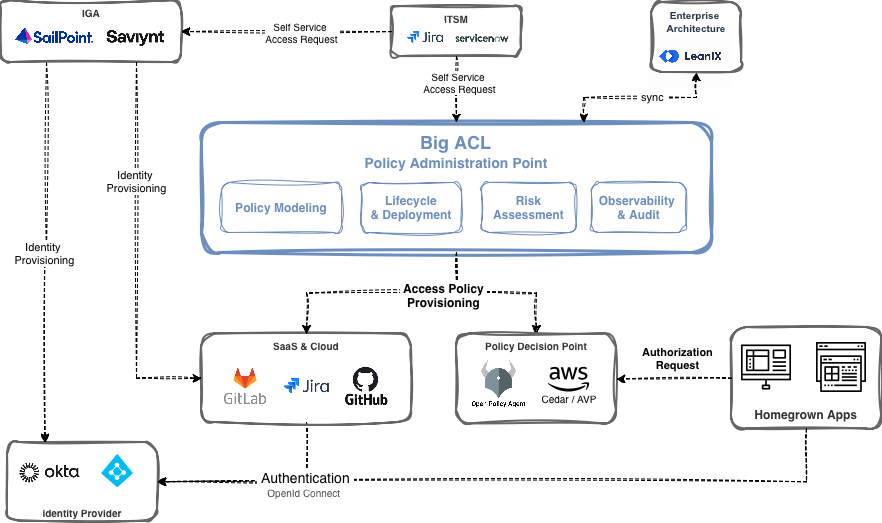
IGA platforms provision identities.
Identity Providers centralize authentication.
Ticketing systems drive access requests and approvals.
Enterprise Architecture provides metadata and ownership.
SaaS & Cloud consume normalized access policies.
Policy Decision Points (OPA, AVP) enforce policies generated by Big ACL.
Built for modern authorization challenges
Whether you're scaling a startup or managing enterprise complexity, Big ACL gives you the tools to handle authorization the right way.
Full deployment history with end-to-end rule traceability — from natural language to formalized policy, Rego translation, test execution, deployment, and decision logs. Immutable verifiable snapshots and SIEM export give auditors everything they need.
Product, engineering, and security teams work from the same policy repository. No more scattered rules across codebases, conflicting interpretations, or tribal knowledge about who can do what.
Stop embedding authorization logic in your codebase. Externalize policies to make your applications cleaner, easier to audit, and simpler to maintain. Change rules without redeploying code.
Developers focus on building features, not reinventing authorization. Big ACL deploys rules directly to your Policy Decision Points (OPA, AWS Verified Permissions), letting product and security teams manage access independently.